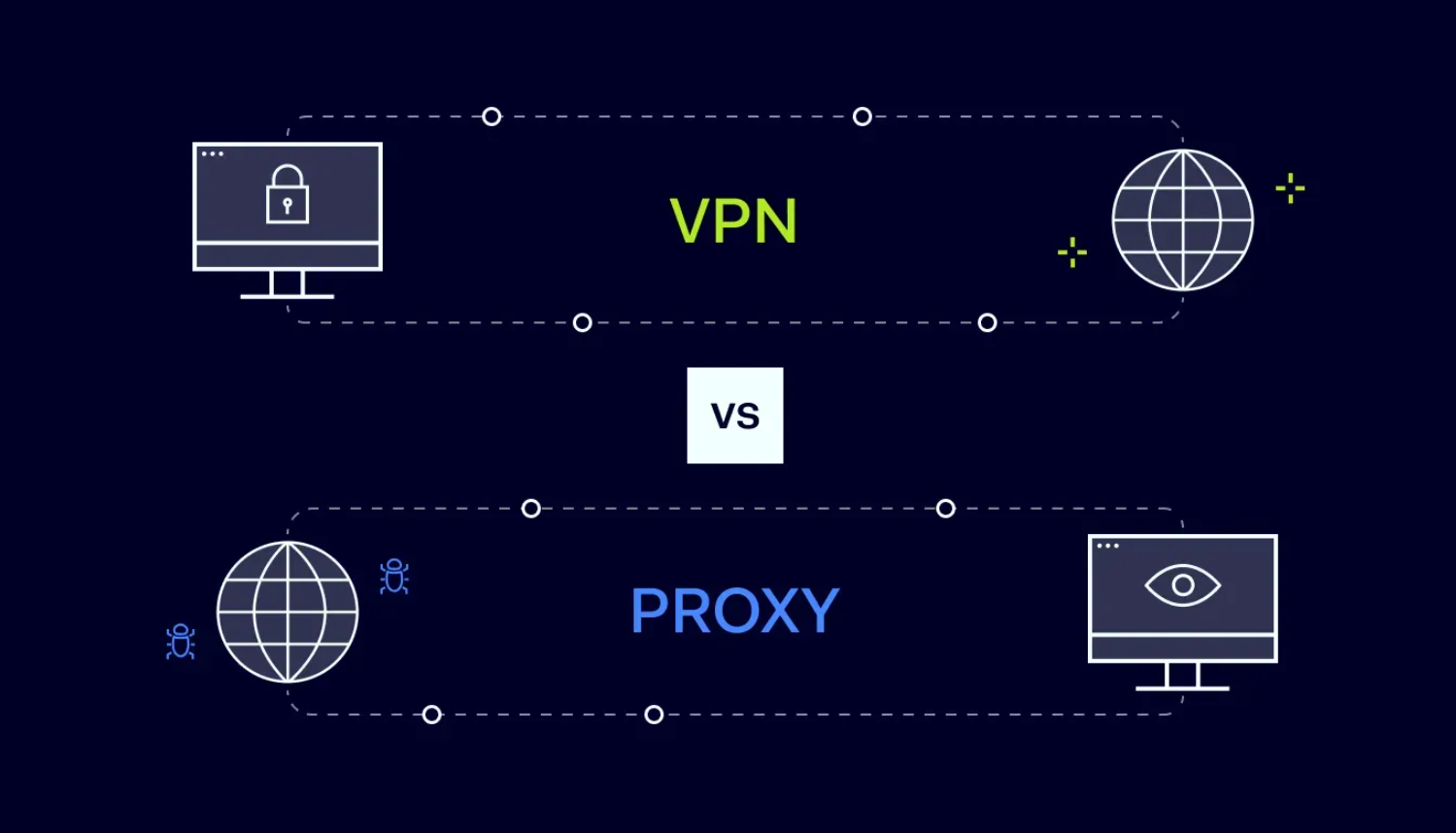
In the modern digital age, the internet feels less like a library and more like a battlefield. Between data trackers, hackers lurking on public Wi-Fi, and streaming services blocking your favorite shows based on where you live, the need for digital camouflage is at an all-time high. You have likely heard the terms “Proxy” and “VPN” thrown around in tech conversations.
Many people use these terms interchangeably, assuming they are just technical jargon for “hiding my location.” This is a dangerous misconception. While they share a common goal—masking your identity—the way they achieve it and the level of protection they offer are worlds apart.
Understanding the proxy vs VPN difference isn’t just for IT professionals; it is essential knowledge for anyone who handles banking apps, sends private emails, or simply wants to browse without Big Tech looking over their shoulder. Let’s dive deep into the mechanics, the risks, and the reality of these two technologies.
The Middleman: What is a Proxy Server?
To understand the difference, we first need to look at the proxy. Imagine you want to buy a limited-edition sneaker, but the store only sells to people in New York. You live in London. So, you ask your friend in New York to go to the store, buy the shoes, and ship them to you.
In this scenario, your friend is the Proxy.
Technically speaking, a proxy server acts as a gateway or an intermediary between you (the client) and the internet (the server). When you use a proxy, your web request goes to the proxy server first. The proxy server then makes the request to the website on your behalf, collects the information, and sends it back to you.
Key Characteristics of a Proxy:
-
IP Masking: The website sees the IP address of the proxy server, not yours.
-
Application Specific: Proxies usually work on an app-by-app basis. You might set up a proxy in your web browser, but it won’t cover your Spotify app or your Windows updates.
-
No Encryption (Usually): This is the critical flaw. Most standard proxies (like HTTP proxies) do not encrypt your traffic. If you are on public Wi-Fi, a hacker can still intercept your data between you and the proxy.
According to a report by PCMag, proxies are often excellent for low-stakes tasks like bypassing a simple region lock on a website, but they are “woefully inadequate” for protecting sensitive personal data.
The Armored Tunnel: What is a VPN?
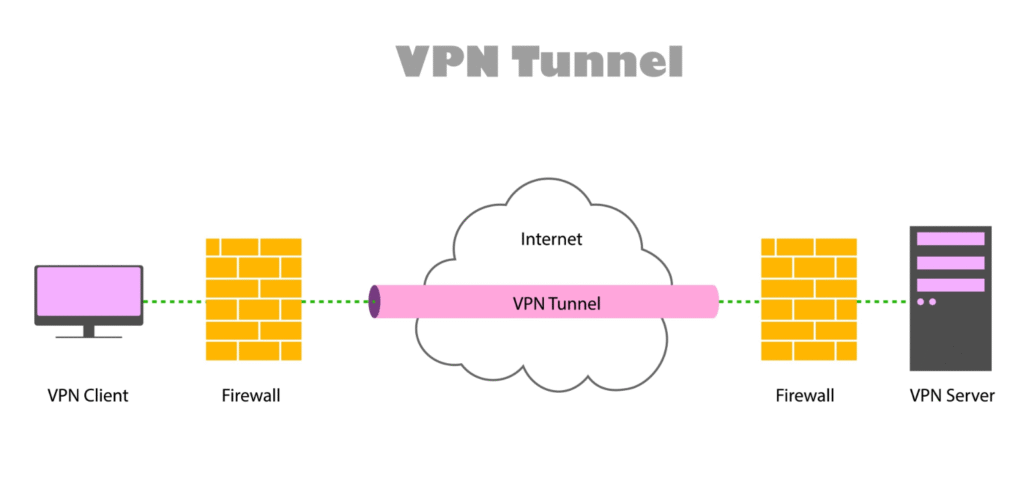
Now, let’s look at the Virtual Private Network (VPN). If a proxy is a friend buying shoes for you, a VPN is an armored truck driving you directly from your house to the store inside a private, underground tunnel.
A VPN creates a secure, encrypted connection between your device and the internet. It doesn’t just reroute your traffic; it scrambles it so that it becomes unreadable to anyone who might be watching—including your Internet Service Provider (ISP), the government, or hackers.
Key Characteristics of a VPN:
-
System-Wide Protection: Unlike a proxy, a VPN captures all traffic leaving your device. This includes your browser, your email client, your games, and background OS services.
-
High-Level Encryption: VPNs typically use military-grade encryption (like AES-256). Even if someone intercepts the data, it looks like gibberish.
-
No-Log Policies: Premium VPN providers operate under strict policies where they do not store logs of your activity, ensuring true anonymity.
As noted by CNET in their cybersecurity reviews, a VPN is the “gold standard” for anyone concerned about digital surveillance or using unsecured networks like those in coffee shops or airports.
The Great Showdown: Proxy vs VPN Difference Explained
Now that we have defined the players, let’s break down the specific areas where they diverge. This is where the proxy vs VPN difference becomes clear and critical for your decision-making.
1. Encryption and Security
This is the deal-breaker. A standard proxy server does not encrypt your traffic. It merely hides your IP address. If you are logging into your bank account using a free HTTP proxy, the owner of that proxy (and potentially your ISP) can see your credentials in plain text if the site isn’t using HTTPS.
A VPN, however, wraps your data in an encrypted tunnel. Even the VPN server owner cannot see what you are doing inside that tunnel if the encryption is handled correctly (though they can see that you are connected).
2. Speed and Performance
There is a common myth that proxies are faster than VPNs. In theory, this can be true. Because proxies don’t have the “overhead” of encrypting and decrypting data, they can be faster.
However, free public proxies are often notoriously slow because they are overloaded with thousands of users simultaneously. Conversely, premium VPNs have optimized their protocols (like WireGuard) to the point where the speed loss is negligible.
3. Cost and Reliability
“You get what you pay for” applies heavily here.
-
Proxies: Often free. However, free proxies are often unstable, go offline without warning, and some have even been caught injecting ads or malware into user sessions.
-
VPNs: While free VPNs exist (and should mostly be avoided), reputable VPNs cost money. This subscription fee pays for server maintenance, advanced security protocols, and support staff.
4. Traffic Coverage
This is often overlooked. If you configure a proxy in Firefox, your Chrome browser is still exposed. Your Skype calls are exposed. Your torrent client is exposed.
A VPN is installed on the operating system (or even the router). Once you click “Connect,” every single byte of data leaving your device is routed through the secure tunnel.
Comparison Table: At a Glance
To make this easier to digest, here is a direct comparison of the features.
| Feature | Proxy | VPN (Virtual Private Network) |
| Primary Function | IP Masking / Bypassing Geo-blocks | Privacy, Encryption, and Anonymity |
| Encryption | None or very weak | High-level (AES-256 usually) |
| Scope | Application-level (Browser only) | Operating System-level (All traffic) |
| Speed | Generally faster (no encryption overhead) | Slightly slower (due to encryption) |
| Cost | Often free | Usually paid subscription |
| Security Level | Low | High |
| Best For | Web scraping, simple region bypass | Public Wi-Fi, Banking, Torrenting |
When Should You Use a Proxy?
Despite the security flaws, proxies aren’t useless. They are lightweight tools for specific jobs. You might prefer a proxy if:
-
You are on a budget: If you have literally zero budget and just need to read a news article blocked in your country, a proxy is a quick fix.
-
Web Scraping: Developers and data scientists often use rotating residential proxies to scrape data from websites without getting their IP banned.
-
Legacy Systems: Some older business networks still rely on local proxies for intranet traffic management.
However, Forbes Tech Council warns that users should treat free proxies with extreme caution, as many operate without clear privacy policies, meaning they could be selling your browsing data to third parties.
When Should You Use a VPN?
For 90% of general users, a VPN is the superior choice. You should absolutely use a VPN if:
-
You use Public Wi-Fi: This is non-negotiable. If you are at a Starbucks or a hotel, a VPN protects you from “Man-in-the-Middle” attacks.
-
You Stream Content: Modern VPNs are much better at bypassing the sophisticated detection systems used by Netflix, Hulu, and BBC iPlayer compared to simple proxies.
-
You Value Privacy: If you don’t want your ISP selling your browsing history to advertisers, a VPN obscures that data.
-
Gaming: A VPN can protect you from DDoS attacks during competitive gaming and occasionally lower ping if the routing is optimized.
The Danger of “Free” Services
A crucial aspect of the proxy vs VPN difference discussion is the economy of free services. Running a server farm costs a lot of money. If a company is offering you a free VPN or Proxy, ask yourself: How are they paying the electricity bill?
Usually, the answer is you.
Free providers often monetize by:
-
Injecting targeted ads into your browser.
-
Logging your activity and selling the data to marketing aggregators.
-
Using your bandwidth as an exit node for other users (effectively turning you into a proxy).
According to a security study highlighted by TechRadar, nearly 40% of free Android VPN apps contained some form of malware or malvertising.
FAQ: Common Questions
Q: Can I use a Proxy and a VPN at the same time?
A: Technically, yes, but it is usually unnecessary and will drastically slow down your connection. It is like wearing two raincoats; you aren’t much drier, but you can barely move.
Q: Does a VPN make me 100% anonymous?
A: No technology offers 100% anonymity. However, a VPN makes it significantly harder to track you. If you combine a VPN with the Tor browser, you achieve near-total anonymity, though speed will suffer.
Q: Which is better for torrenting?
A: Definitely a VPN. A proxy might hide your IP from the tracker, but because it doesn’t encrypt the traffic, your ISP can still see that you are torrenting and may throttle your speed or send you a copyright notice.
Q: Do proxies hide my search history from Google?
A: No. If you are logged into your Google account, Google tracks your history regardless of your IP address. A proxy only hides your location, not your identity if you are logged into services.
Final Verdict: Which One Wins?
When analyzing the proxy vs VPN difference, the winner depends entirely on the battle you are fighting.
If you are a developer needing to bypass a quick IP check or scrape some data, the Proxy is your lightweight, agile friend. It is a specific tool for a specific task.
However, for the average internet user who wants to browse freely, secure their banking data, watch global content, and keep their personal life private, the VPN is the undisputed champion. It offers a holistic shield that covers your entire digital footprint, not just a single browser window.
In a world where data is the new gold, paying a few dollars a month for a reputable VPN is the cheapest insurance policy you can buy for your digital life. Don’t settle for a leaky proxy when you can have an armored tunnel.
 How to Access Blocked Sites on Android Without Root
How to Access Blocked Sites on Android Without Root Yandex Japan vs. Yandex Russia: Key Differences Explained
Yandex Japan vs. Yandex Russia: Key Differences Explained How to Check for IP Leaks When Using a VPN (WebRTC & DNS)
How to Check for IP Leaks When Using a VPN (WebRTC & DNS) How to Rewatch a TikTok Live: Complete Guide to Replays, Downloads, and Privacy
How to Rewatch a TikTok Live: Complete Guide to Replays, Downloads, and Privacy Want to Borrow Rp1 Million? Here’s How to Easily and Quickly Borrow DANA Balance
Want to Borrow Rp1 Million? Here’s How to Easily and Quickly Borrow DANA Balance What is Web 3.0? A Comprehensive Look at the Fair, Open, and Single-Boss-Free Internet of the Future
What is Web 3.0? A Comprehensive Look at the Fair, Open, and Single-Boss-Free Internet of the Future Free VPN That Works on Netflix: Honest Guide for 2025
Free VPN That Works on Netflix: Honest Guide for 2025